| 일 | 월 | 화 | 수 | 목 | 금 | 토 |
|---|---|---|---|---|---|---|
| 1 | ||||||
| 2 | 3 | 4 | 5 | 6 | 7 | 8 |
| 9 | 10 | 11 | 12 | 13 | 14 | 15 |
| 16 | 17 | 18 | 19 | 20 | 21 | 22 |
| 23 | 24 | 25 | 26 | 27 | 28 |
Tags
- Symmetric key algorithm
- CTF
- c
- NFPC
- DefCon 21
- 대칭키암호
- php
- python
- network forensic
- Stream cipher
- Symmetric key
- 파이썬 문법
- 웹
- Defcon
- 포렌식
- 파이썬
- block cipher
- C언어
- 파이썬 문제
- WEB
- forensic
- Symmetric key crypto
- 대칭키 암호
- 암호학
- 암호
- 네트워크
- 암호수학
- The python challenge
- 파이썬 공부
- pythonchallenge
Archives
- Today
- Total
목록round4 (1)
Hardner
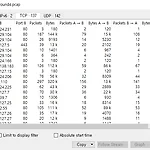 DEFCON 21 Round4 NFPC: Write up
DEFCON 21 Round4 NFPC: Write up
DEFCON 2013 Network Forensics Puzzle Contest: Mystery Date Gregory, still unsure of Betty's true identity, meets with a group identifying themselves as Betty's Associates. They gave him a list of demands including numbers to bank accounts, and additional secret documents. Betty's Associates told Gregory he will be provided with information regarding the delivery of the goods. Use the Round 4 pac..
Computer/Forensic
2019. 7. 16. 22:39
